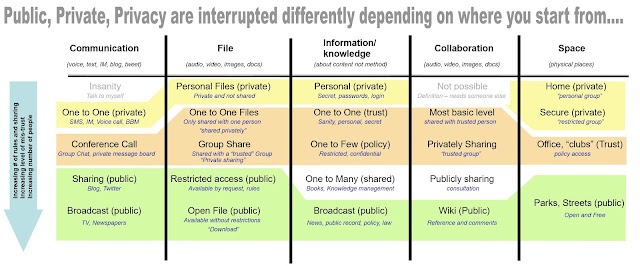
11th June : Identity London workshop covering vrm, personal data, lockers, pii, busienss models...
As we have a large and growing group in the UK and London of those interested in: identity, user centric identity, internet identity, vrm, personal data, digital lockers, digital footprint, personal identifiable data (pii) and personal data eco-systems…. And as an outcome from Doc visit to London in April we have decided to try and bring the community together and start a regular (monthly) meet-up/ open working space/ un-conference/ discussion/ for us to meet up and move forward with sharing and achieving. This also builds on a workshop Iain Henderson and I put on at Innovation Warehouse on Personal Data Store interoperability in April ( write up by Phil is here ) and so the outcome is that we have decided that we should do a wider reaching day with Kaliya Hamlin @IdentityWoman when she was in London with Drummond Reed, Phil Windley and many others for the WEF tiger team on Personal data. The purpose is to move forward the conversation, solutions and projects and f...