The radical shift from profit motivated greed to purpose driven awareness and the impact on the 4 P's in a marketing mix!
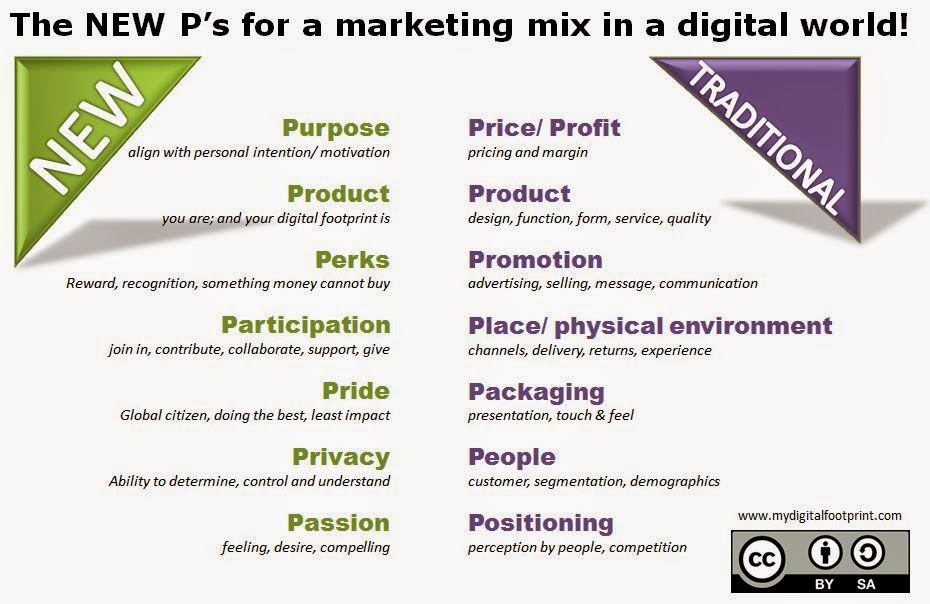
Tony Fish @My Digital Footprint When we were chatting about a collaborative digital business model, my nephew Chris challenged me with this statement “ I can't understand what the consumer gets for helping others though! ” I had just shared with him a business that raised $10m which allows people to help people for free. I was rather hoping that his digital youthfulness was about to surprise me and provide me with a deep native understanding of being-digital and offer me some insights to the future; but his mind has already been corrupted by out of date, but classical business/ marketing, education. As we continued to debate digital first as I structured out an update to classical marketing, as is set out below. There is an awful lot written and taught about the traditional 1960’s marketing mix tool which is commonly known as the 4, 5, 6, 7 and even 8 P’s of marketing. A quick read of Wikipedia gives all the basics. A re-write that never really caught on in the 1990...